Security Services
IT organizations are building, maintaining and improving their network defenses against internal and external malicious users and attackers every day. While understanding how well these defenses withstand adversaries, is imperative to keep your fortress secure.
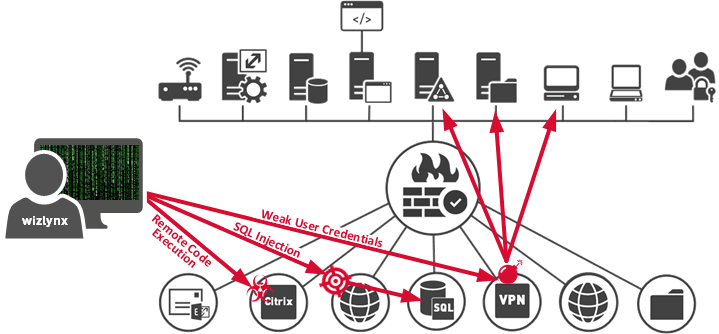
wizlynx group takes the time to understand our client’s business and think like an attacker would. This allows us to gain a holistic overview, as well as a technical point of view. Using set objectives, we will identify the weakest link first, and then escalate until one or several bastions fall, and we gain privileged access to information or systems.
Our penetration testing services leverage a hybrid approach composed of automated and manual testing methods. Attempts to gain privileged access to firewalls, networks and respective devices, servers, IoT, web applications, and other points of exposure will be conducted in a safe and controlled manner, while exploiting identified vulnerabilities. Once a vulnerability has been successfully exploited, our security analysts will attempt to increase their foothold by launching succeeding exploits to gain higher levels of privileges and deeper access to electronic assets and information.
Comprehensive penetration test of your web applications, web services and APIs that may be used to store and access critical business information, with the goal to identify and exploit web-borne vulnerabilities. Our pen-testers will use advanced skills and techniques required to test modern web applications and next-generation technologies.
Evaluation of your internal or external information assets’ ability to withstand attacks. Our world-class penetration testers, armed with the same techniques as cybercriminals, will attempt to break into your network, IT infrastructure, cloud environment, and servers to raise awareness about vulnerabilities and the effects of exploitation, as well as end-user adherence to security policies.
Security review of your mobile applications to identify vulnerabilities specific to mobile computing environments, such as those defined by the Open Web Application Security Project (OWASP) and other emerging industry standards.
Comprehensive wireless penetration testing services, ranging from traditional Wi-Fi networks to specialized wireless systems, which include identifying and exploiting vulnerabilities and providing guidance to strengthen such identified weaknesses.
Our thick-client penetration testing services are designed to provide a comprehensive security assessment of your application, covering all layers from the client-side to data in transit and server-side. Our team of experienced pen-testers will perform an in-depth analysis of your thick-client application to identify and exploit vulnerabilities.
Our Active Directory penetration testing services are designed to identify weaknesses in Microsoft Windows Active Directory environments that could lead to privilege escalation and domain dominance situations. Our experienced pen-testers will use advanced techniques and tools to assess the security of your Active Directory environment, including identifying weaknesses in authentication, authorization, and access control mechanisms.
Information gathering about the target organization, as well as identify underlying components such as operating systems, running services, software versions, etc. The following is a non-inclusive list of items that will be tested to allow us to craft our attack in an informed fashion, elevating our probability of success:
Assessment that consists of evaluating the information assets in scope against 80'000+ vulnerabilities and configuration checks, in addition to CWE/SANS TOP 25 Most Dangerous Software Errors and OWASP Top Ten vulnerabilities. wizlynx group uses several vulnerability scanners, as well as manual techniques, to test the many services that are reachable via the network such as SMTP, HTTP, FTP, SMB, SSH, SNMP, DNS, etc. The following vulnerability types can be identified (non-inclusive list):
Service-Side Exploitation
Network Manipulation & Exploitation
Identity & Authentication Weakness Exploitation
Privilege Escalation
Using a hybrid approach (automated and manual testing), our security analysts will attempt to gain privileged access to the target systems in a controlled manner by exploiting the identified vulnerabilities in previous phase “Vulnerability Identification”.
Refers to testing a system without having specific knowledge of the inner workings of the information asset, no access to the source code, and no knowledge of the architecture. This approach closely mimics how an attacker typically approaches a web application at first. However, due to the lack of application knowledge, the uncovering of bugs and/or vulnerabilities can take significantly longer and may not provide a full view of the application's security posture
Refers to testing the system while having some knowledge of the target asset. This knowledge is usually constrained to the URL of the application, as well as user credentials representing different user roles. Greybox testing allows focus and prioritized efforts based on superior knowledge of the target system. This increased knowledge can result in identifying more significant vulnerabilities, while putting in much less effort. Therefore, greybox testing can be a sensible approach to better simulate advantages attackers have, versus security professionals when assessing applications. Registered testing allows the penetration tester to fully assess the web application for potential vulnerabilities. Additionally, it allows the tester to verify any weaknesses in application authorization which could result in vertical and/or horizontal privilege escalation.
Refers to testing the system while having full knowledge of the target system. At wizlynx group, our whitebox penetration test is composed of a greybox test combined with a secure code review. Such assessments will provide a full understanding of the application and its infrastructure’s security posture
All findings will be documented in a final report, and then compared with a strengths/weaknesses profile against international standards for IT & Cyber Security. The identified weaknesses will be assessed and supplemented with recommendations and remediation actions, as well as prioritized according to the risk associated. The final report will be discussed during a presentation with you. The report will include a comprehensive and meaningful C-level summary of the executed security audit or penetration test. Additionally, it will include all detailed results with respective evidence and recommendations for future security measures.
Greybox Web Application Pentest of multiple applications & APIs which streamlines the prior authorization process for all pharmacies and prescribers, optimize specialty pharmacy operations, prescription workflow, and overall patient management
Internal Vulnerability Assessment of a corporate network.
Penetration Testing of an Microsoft Power BI app.
wizlynx's security consultants and penetration testers hold the most recognised certifications in cyber security and penetration testing industry such as: SANS/GIAC GPEN, GWAPT, GCIH, GMOB, OSCP, CEH, CISSP, CISA and more!






