Security Services
Traditionally, ICS and SCADA systems used proprietary control protocols and very specialized hardware and software making them not compatible with IT networks. In the past, Operational Technology (OT) networks were physically secured areas and devices were not connected to the IT network. Therefore, providing security was mainly about ensuring safety to human and environmental accidents.
Over the last decade, though, the IT/OT convergence occurred, allowing ICS environments to become more sophisticated and connected. However, the OT's modernization through IT integration brought along its security risks and susceptibility to cyber-attacks perpetrated by external threat actors.
Because ICS /SCADA environments have a direct effect on the physical world and can pose in certain cases a significant risk to the health and safety of human lives and serious damage to the environment, as well as serious financial issues, it is of utmost importance to ensure that a proper security level is applied.
For this reason, wizlynx group is offering an in-depth but minimally invasive review of your Industrial Control Systems (ICS) / Operational Technology (OT) environment against ICS best practice frameworks such as NIST Guide to Industrial Control Systems (ICS) Security Rev 2. This assessment will allow you to identify and understand your weaknesses and vulnerabilities affecting your ICS environment and establish an achievable plan to improve your cyber security posture. Our services rely on highly skilled cyber security analysts and pen-testers with extensive experience, both in defense and offense.
Leave no stone unturned with wizlynx’s security assessments!

Our security assessment for Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) systems is highly inspired from various best practice frameworks (CIS Critical Security Controls, NIST Guide to Industrial Control Systems (ICS) Security Rev 2, ISO/IEC 27001/27003, etc.), tailored and adapted to the possibilities and capacities of any company to operate a secure OT environment. Our ICS security assessment will mainly focus on the following areas:
Tracking and management of all hardware devices connected to the network is implemented so that only authorized devices are given access, and unauthorized and unmanaged devices are discovered and stopped from accessing the network.
A comprehensive ICS vulnerability management strategy is documented and enforced and includes procedures to timely implement and process patches and updates on critical assets.
Ensuring the OT network is separated either logically or physically from the IT network and the OT network is segmented as per NIST SP 800-82 recommendations. Traffic between segments should only be allowed by following the principle of least privilege.
Use of a multilayered boundary defense relying on firewalls, proxies, web application firewalls, network-based IPS and IDS inspecting traffic both inbound and outbound and looking for attacks and evidence of compromised machines.
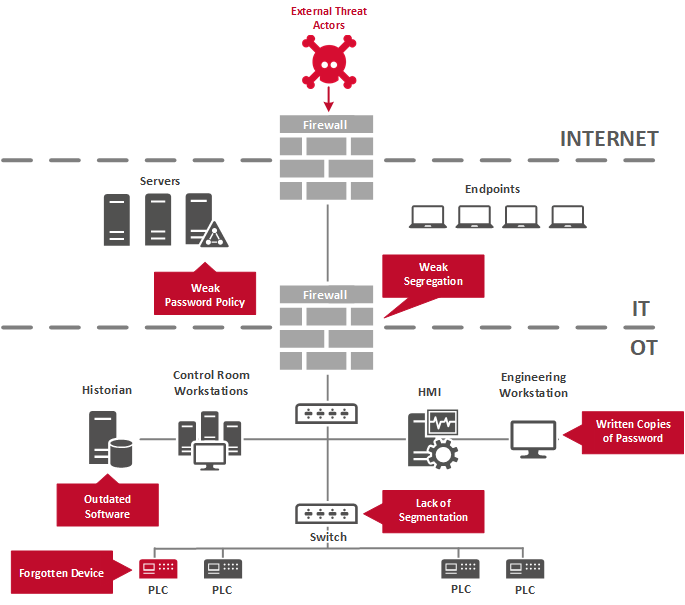
Security best practices for handling passwords and credentials are employed such as the usage of multi-factor authentication for remote access and critical accounts, enforcement of a strong password policy, absence of default and/or shared accounts, etc.
Usage of a secured/hardened configuration for different asset types deployed in the IT and OT network using a rigorous configuration management and change control process.
Collection, management, and analysis of audit logs of events that could help detect, understand, or recover from an attack.
Deployment of a solution which controls the installation, spread, and execution of malicious code at multiple points in the enterprise.
All findings of the ICS Security Assessment will be documented in a final report, and then compared with a strengths/weaknesses profile against international standards for IT & Cyber Security. The identified weaknesses will be assessed and supplemented with recommendations and remediation actions, as well as prioritized according to the risk associated. The final report will be discussed during a presentation with you. The report will include a comprehensive and meaningful C-level summary of the executed operational technology environment. Additionally, it will include all detailed results with respective evidence and recommendations for future security measures.

wizlynx's security consultants and penetration testers hold the most recognised certifications in cyber security and penetration testing industry such as: SANS/GIAC GPEN, GWAPT, GCIH, GMOB, OSCP, CEH, CISSP, CISA and more!






