Security Services
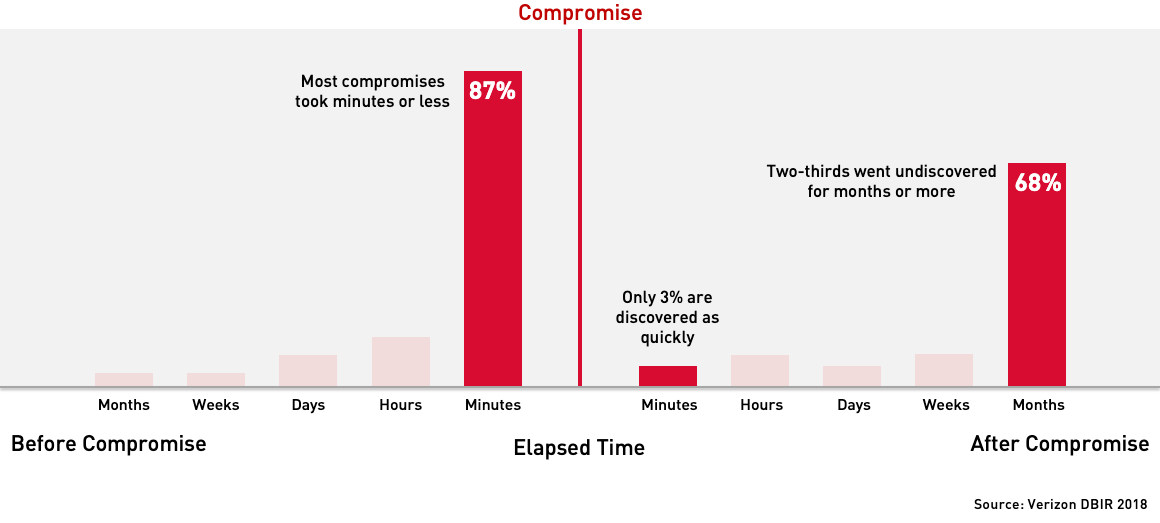
Over the last few years, the complexity, sophistication, and stealth of new cyber security threats have grown rapidly. Conventional computer protection technologies have become less effective and are no longer able to guarantee the security of company assets. This is confirmed by recent breach investigation reports which clearly indicate that more than two-thirds of confirmed data breaches went undiscovered for months or more. Only 3% of the compromises were detected in minutes.
Is an attacker currently in your environment without your knowledge?
Our compromise assessment service has been designed to answer that question. Our threat hunters will combine state-of-the-art targeted cyber threat intelligence, network, and endpoint detection to review your organization’s infrastructure, systems and applications in order to identify malware, back-doors, unauthorized access, and indicators of compromise which could confirm an active or recent security breach within your environment.

All findings of the ICS Security Assessment will be documented in a final report, and then compared with a strengths/weaknesses profile against international standards for IT & Cyber Security. The identified weaknesses will be assessed and supplemented with recommendations and remediation actions, as well as prioritized according to the risk associated. The final report will be discussed during a presentation with you. The report will include a comprehensive and meaningful C-level summary of the executed operational technology environment. Additionally, it will include all detailed results with respective evidence and recommendations for future security measures.

wizlynx's security consultants and penetration testers hold the most recognised certifications in cyber security and penetration testing industry such as: SANS/GIAC GPEN, GWAPT, GCIH, GMOB, OSCP, CEH, CISSP, CISA and more!






