Security Services
Companies are more and more aware about the threats derived by possible cyber-attacks which are evolving rapidly in sophistication, stealth, and complexity. For this reason, small, medium and large organizations are deploying defensive layers, mechanisms and solutions to prevent cyber threats from occurring: firewalls, IDS, IPS, and other systems compose the defense line against malicious operations. To these technical devices, we can add the human layer - the so-called “blue team” - that configures, maintains and operates on this infrastructure. There is one problem though: this defense works with different interaction and processes, that in some cases, are extremely complex and is mainly tested only when a harmful and stressful incident occurs.
How can we be sure your defenses work properly? And how can you know if your internal security team and security operations center (SOC) is really prepared to detect and respond to a targeted attack?
Our Intelligence-led Penetration Testing and Red Teaming assessment is the practice of attacking a problem from an adversarial point of view and follows different approach from a typical security assessment. It relies heavily on well-defined tactics, techniques, and procedures (TTPs), which are of utmost importance to successfully emulates realistic threat or adversary.
Our services rely on highly skilled security professionals, senior penetration testers, and ethical hackers from different backgrounds and various skills with extensive experience, in both defense and offense, combining unique mindsets for the same goal: YOUR SECURITY.

The rationale for red teaming is to be defined during this phase. There is a need before engaging in any activity to assess the customer’s current needs and the scope of the actions that will be undertaken. This is the phase during which limitations such as the duration, the legal boundaries and prohibited actions have to be determined. This can be compiled under the form of a “rules of engagement” document
Once the scope has been agreed, testing can commence with the attack preparation phase introducing Threat Intelligence. Threat-intelligence based scenarios mimicking real-life cyber adversaries are essential to the success of testing activities and are the output of the generic threat landscape and targeted threat intelligence.
Multiple attack scenarios are created by using the generated Threat Intelligence to determine the most probable steps that real world cyber attackers would use to compromise the target customer and critical functions along with the MITRE ATT&CK framework.
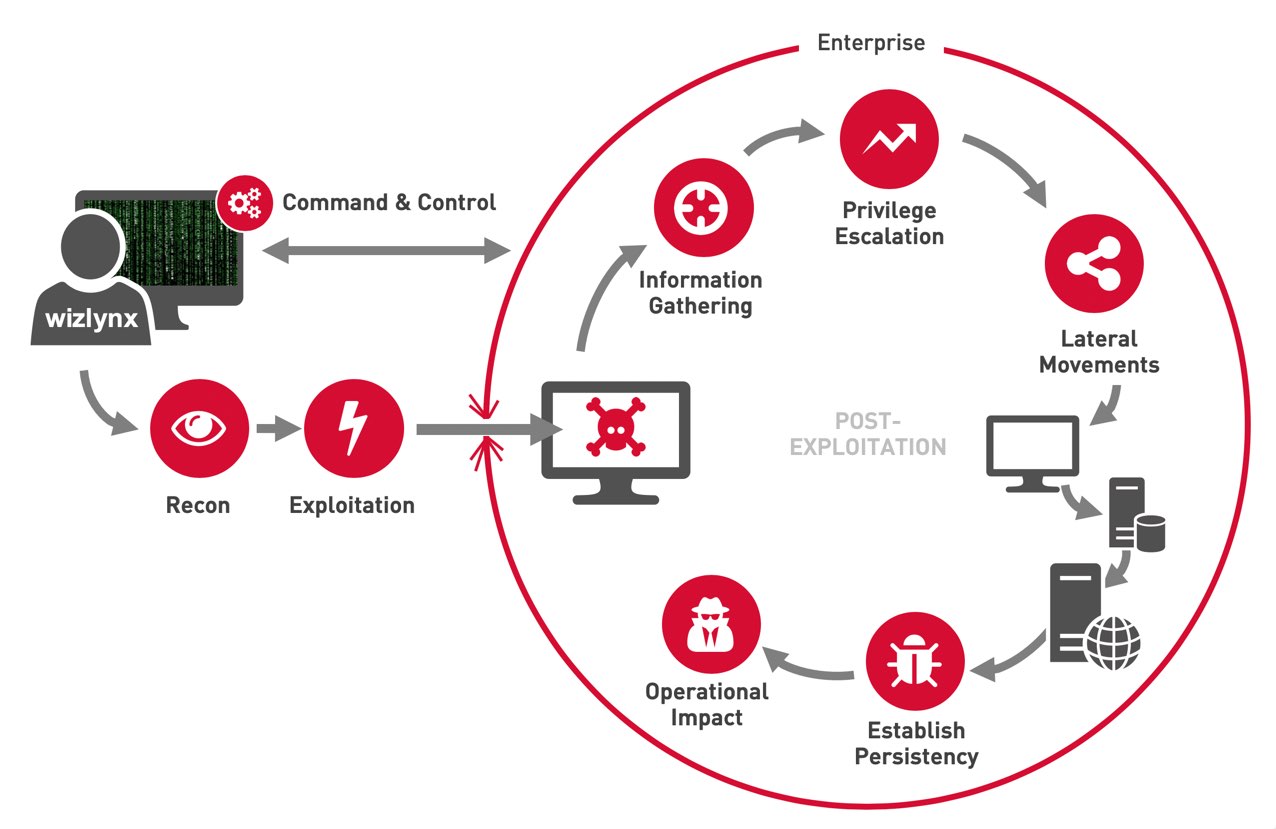
Each phase is broken down in sub-phases representing the attack execution workflow as shown below:
The report will include a comprehensive and meaningful C-level summary of the executed Intelligence-led Penetration Testing and Red Teaming assessment which will include security strengths, comprehensive analysis of organizational capability, with recommendations for remediation and enhancements.
The detailed report will also include the actual scenario-based attack as it played out, listing the attack elements (with respective evidence) that were critical to the success of the attack, such as the weaknesses discovered that enabled the Red Team to progress to the next stage.
Finally, a complete logbook of all actions performed by the Red Team will be provided to the customer containing timestamps, source & destination IP addresses, tools, command, description, output, result, etc.

Although Intel-led Penetration Testing and Red Teaming is offensively focused, it is ultimately used as a tool to improve security & Blue Team. A workshop with all necessary party’s representatives is organized to discuss the red teaming engagement and findings.
The workshop has for main objective to go through all actions performed by the red team. For actions undetected by blue team, the goal is to understand why detection mechanism and procedures failed, in order to take out lessons learned and improvement actions.
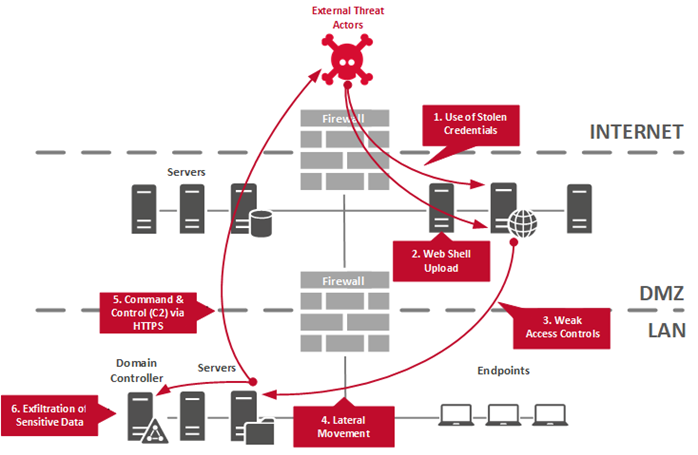
Breach-Assumed Red Teaming engagement composed of two scenarios. The first scenario consisted in emulating an authenticated attacker with physical access to the customer’s office premise such as a staff employed by cleaning company. The second scenario consisted in mimicking an attack, as a low-privileged domain user with access to the customer’s network.
Given the two scenarios, the objective was to identify if an attacker could penetrate our customer’s defenses and gain unauthorized access to organization’s Domain Controller within the given timeframe.
Red Team Operations and Threat Emulation Services following a Breach-Assumed scenario of a water, gas, and electricity provider which consisted in emulating an internal threat of a user having access to network sockets. The main objective was to identify if sensitive information can be discovered and exfiltrated as well as if the ICS/OT network can be accessed by the attacker.
Intelligence-Led Penetration Testing & Red Teaming composed of the Get-In, Stay-In and Act phase against the infrastructure and employees of an IT Service Provider. The Red Teaming engagement’s Get-In phase included both vulnerability identification and exploitation as a mean to break into the customer’s network but also advanced spear-phishing attacks against key employees. The main objective defined during the engagement was to access and exfiltrate sensitive data and assess the customer security operations center’s capability to detect our attacks.
wizlynx's security consultants and penetration testers hold the most recognised certifications in cyber security and penetration testing industry such as: SANS/GIAC GPEN, GWAPT, GCIH, GMOB, OSCP, CEH, CISSP, CISA and more!






