Your Data Can Be Kidnapped Too… Ransomware in Action
According to Wikipedia “Ransom is the practice of holding a prisoner or item to extort money or property to secure their release, or it...
Can a Refrigerator Compromise the Security of Your Company?
The internet has been invented for a while now. It connected people, images, recording, games, books, and commerce. By people, for people. With the...
PwnTillDawn, The Penetration Testing CTF Events for 2022
wizlynx group is thrilled to announce that PwnTillDawn will be back very soon hosting a new CTF...
Mobile Security: Connect your brain, not only your device!
Mobile devices often create opportunities. We are now able to access the web from the bus, buy stock options at the hairdresser, check emails...
How does Cyber Threat Intelligence relates to data privacy and data...
Your digital identity and Personally Identifiable Information can be used by malicious actors for a variety of purposes.
Let’s...
NowProtected Secure Browser
NowProtected
For your eyes only!
E-Banking has become a necessity for many people in today’s world. It minimizes the need to physically visit your bank and...
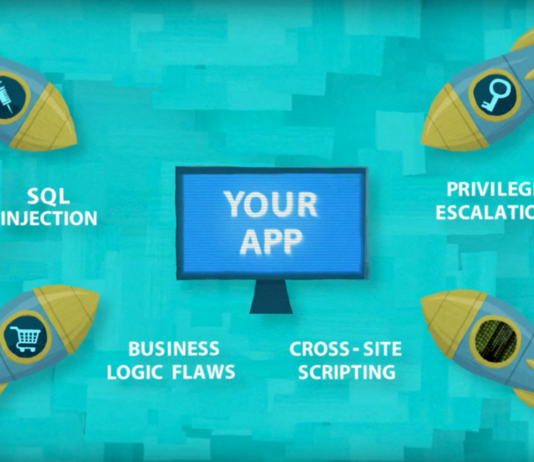
Ethical Hacking & Penetration Testing Services
Leave No Stone Unturned!
IT Security is not a feature but a state of mind. It is our vocation. By adopting latest hacking methods and...
The Invisible Threat: Understanding Remote Hacking and How to Safeguard Your...
In today's increasingly digitalized society, mobile devices have become indispensable, connecting us with loved ones and powering business transactions. However, this reliance on mobile devices brings with it a heightened risk of cyber threats, notably remote hacking. In this article, we delve into the various techniques employed by cybercriminals to remotely infiltrate your phone, from exploiting system vulnerabilities and weak passwords to utilizing cunning social engineering tactics like phishing. The alarming statistics from a Check Point Software study reveal that 97% of organizations encountered mobile threats, emphasizing the pressing need to protect against these risks. Learn how you can safeguard yourself and your organization's sensitive data with essential cybersecurity measures.
2023 Top Cyber Security Threats and Solutions
As we embrace digitalization, organizations have become more vulnerable to cybercrime. Not only are businesses at risk but governments and individuals are...
What Does wizlynx group Do? A beginner’s guide to our cyber...
We have all grown accustomed to the convenience of the digital world, always ready at the tap of our fingertips. However, as...