
Together with your internet-facing web apps, you are undeniably the #1 target of a cyber attacker to either break into your computer and corporate network, or access sensitive information using social engineering techniques.
But what is social engineering exactly? Before digging any deeper, let’s start with a quote from Kevin Mitnick, one of the most famous social engineers in the world:
”Social engineering uses influence and persuasion to deceive people by convincing them that the social engineer is someone he is not, or by manipulation. As a result, the social engineer is able to take advantage of people to obtain information with or without the use of technology. “
In this post, we will cover mostly social engineering’s email phishing tactics & techniques. Surprisingly, social engineering and email phishing have been around for years and yet, they are still very effective techniques. But why?
First of all, it is important to understand our relationship with emails. In today’s world, email is one of the primary ways we communicate. We not only use it every day for work, but to stay in touch with our friends and family. In addition, email is how most companies provide online services, such as confirmation of your online purchases or availability of your bank statements. Since so many people around the world depend on email, it is natural for such communication channels to become one of the primary attack methods used by cyber criminals.
But who is really to blame? Many people tend to put blame on the user receiving the phishing email, but are they the responsible or the weak-link, as we often call it?
Attackers work hard to make their phishing emails convincing. For example, they will make their email look like it came from someone or something you know, such as a friend, a work colleague, or a trusted company you frequently communicate with. As an example, cyber criminals will often use state-of-the-art methods such as sending emails or hosting malicious apps with domains that look very similar to products or software-as-a-service you use (e.g. 0nedrive.com). They might do the same with your own domains using a technique known as typosquatting which consists in adding, modifying or removing characters in the legitimate domain name (e.g. giantnationalbank.com -> giantnationalbamk.com).
But that’s not all! Cyber criminals leverage the fact that you receive a large amount of emails and might not have the time to carefully inspect each and every email you receive. They will even use advance reconnaissance techniques to understand with whom you might be speaking with, for what purpose, and leverage this relationship to deceive you. Finally, they will use tragic moments to their advantage, such as the COVID-19 pandemic, financial crisis, natural disasters, etc., to deceive you when you are the most distracted and vulnerable…
Multiple Flavors of Email Phishing
There are several ways attackers use phishing to get what they want:
Malicious Links: The attacker’s objective is to compromise your device. To do this, they send you a phishing email containing a link. If you click on the link, you will be taken to a website that launches an attack on your device attempting to exploit vulnerabilities that might affect your web browser or web browser components such as Flash, Silverlight, etc.
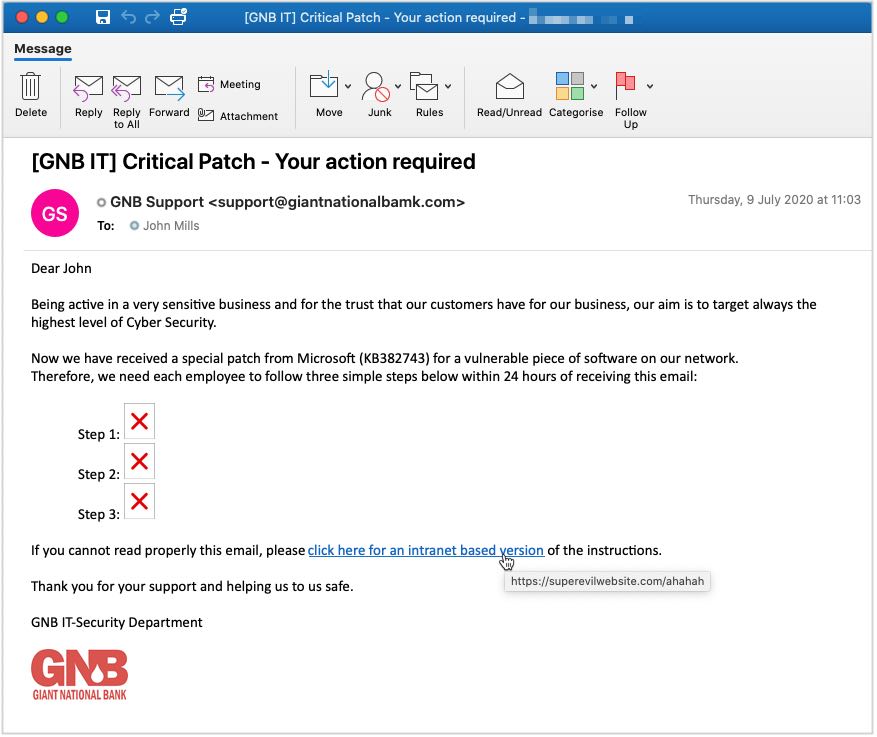
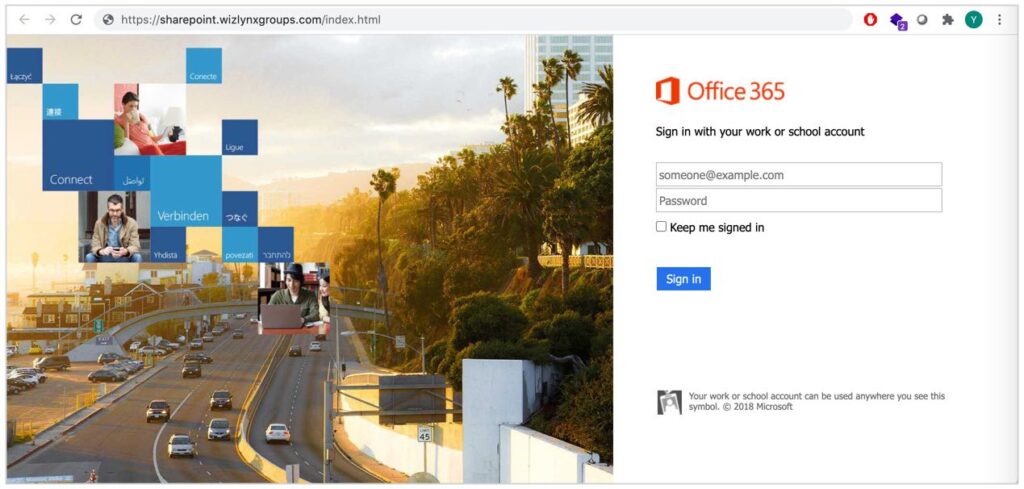
Harvesting Sensitive Information: The social engineer’s goal is to collect your sensitive and personal information, such as your passwords, credit card numbers or banking details. To do this, they email you a link that redirects you to a website that appears legitimate and that looks very similar to a real website you regularly use. This website then asks you to provide your account information or personal data which will be sent to the attacker.
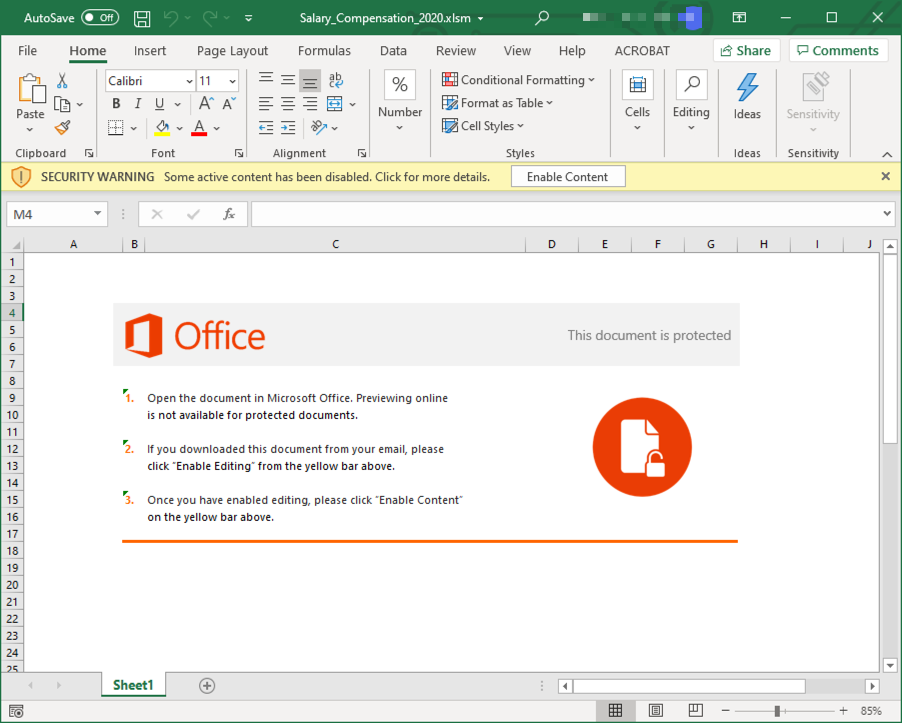
Malicious Attachments: The attacker’s goal is the same: to compromise and take control of your device. But instead of a link, the attacker emails you an infected file, such as a Word or Excel document. Opening the attachment triggers the attack, potentially giving the attacker control of your system.
How Effective is Email Phishing?
Our Social Engineering Assessments and Red Teaming exercises speak for themselves. In 2020, we have conducted many assessments, mainly spear-phishing oriented and the results are rather alarming:
- When sending an email with an attachment, such as an Excel file with Macro, approximately 35% of the target users enabled the VB Macro. As an example, on the last campaign we ran, 262 users over 702 enabled the Macro.
- When sending an email containing a hyperlink, an average of 30% clicked on the link. The last campaign of this type ran by wizlynx group tricked 102 users of 401 into clicking on a link leading to a potentially malicious website.
- When sending an email redirecting users to a website
mirror, around 15% provided their username and password. As an example,
on the last campaign we ran, 71 users of 401 typed and submitted their user
credentials to our rogue web site looking similar to a website they are
regularly using.
The news is also a great indicator of how effective email phishing can be:
- In 2014/2015, the great bank robbery (also known as Carbanak APT) hit up to 100 financial institutions with a total financial loss estimated as high as $1bn. Attackers used spear phishing emails with malicious attachments against employees of the targeted financial institutions. https://securelist.com/the-great-bank-robbery-the-carbanak-apt/68732/
- In 2020, the global cybersecurity training and certifications SANS Institute’s phishing attack led to the theft of 28,000 records of personal information (PII) for SANS members. https://www.bleepingcomputer.com/news/security/sans-shares-details-on-attack-that-led-to-their-data-breach/
- As per the Verizon’s 2020 Data Breach Investigations Report (DBIR), 22% of confirmed breaches included social attacks.
What Should We Do To Prevent Email Phishing?
Preventing email phishing completely is, in our opinion, a utopia. A multi-layer defense approach should be taken to limit the chances of your employees being a victim of phishing and decrease the potential damages of phishing attacks.
- Your internal documentation and policies should be adjusted to provide information to your employees on how to spot phishing emails, how to report them, and what to do in the situation they interacted with a phishing email. Since it is very likely that one of your associates will eventually become a victim of phishing, encouraging the report of incidents without consequences to the reporter is vital to ensure the bleeding can be quickly stopped.
- The end-users should be properly educated. Regular cyber security awareness trainings, as well as social engineering assessment and email phishing simulations should be conducted.
- Two-Factor Authentication should be used and enforced wherever possible.
- Ensure your email server is properly hardened to block most phishing emails (enable SPF, DKIM, DMARC, set up a Spam filter, disable relaying, enable attachment restrictions, etc.).
- End-user devices should be kept up-to-date. This includes browsers and browser components, such as Flash, Silverlight, Java, etc.
- End-user devices should be protected by an enterprise grade endpoint security solution offering complete protection, including antimalware, anti-phishing, web control and firewall.
- Consider adding a warning in the subject or body of emails originating from outside your organization.
wizlynx group has extensive experience in developing and conducting cyber security awareness trainings, as well as social engineering and email phishing simulations. Our services rely on highly skilled security professionals and penetration testers with long-lasting know-how, both in defense and offense, to create realistic trainings and phishing scenarios. wizlynx group relies on Phishlynx, an in-house developed solution, to assist us during Social Engineering Assessments.
Contact us if you seek advice to increase your security posture and assess but also improve your employee’s readiness to withstand common phishing attacks.
Léon C.
Cyber Security Consultant & Researcher @ wizlynx group




