
With the evolution of cybercriminals, the complexity and sophistication of cyberattacks have increased. Attackers constantly develop new techniques and tools to gain unauthorized access to sensitive information and systems while evading detection. Furthermore, they have expanded their range of targets! As a result, the demand for offensive cybersecurity services has increased. Utilizing offensive cybersecurity tactics effectively, such as vulnerability assessments or penetration testing, can greatly benefit your organization in identifying and addressing system vulnerabilities.
Understanding offensive cybersecurity services
At wizlynx group, we pride ourselves in providing valuable insight into these scenarios. We constantly study and emulate real-world cybercriminal tactics, techniques, and procedures for your advantage. Now, a vulnerability assessment and a penetration test represent two different approaches to cybersecurity. Both vulnerability assessments and penetration testing are crucial components of a comprehensive cybersecurity strategy that helps evaluate the security of your organization’s assets.
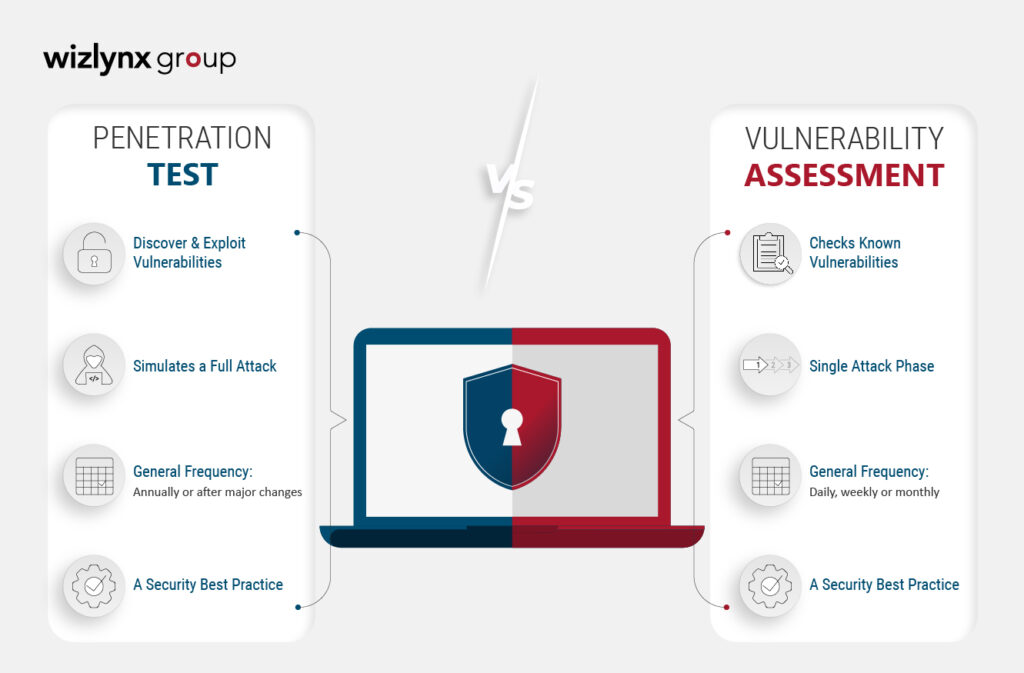
On one hand, a vulnerability assessment is a systematic examination of a computer system to identify and evaluate known security vulnerabilities. Its purpose is to identify weaknesses in a system that could be exploited by an attacker. It can also provide recommendations for mitigating those vulnerabilities. These typically use automated tools to scan a system for known vulnerabilities and may also include manual testing.
On the other hand, a penetration test -or pentest– simulates a cyber-attack on a system to evaluate its defenses. Its purpose is to examine your system’s capacity to safeguard your assets from attackers. It can also help assess the impact of successful exploitation. Unlike a vulnerability assessment, a pentest focuses on attempting to exploit those vulnerabilities to gain unauthorized access to the system. The measuring of control effectiveness is not the main goal. Learn more on how to prepare for a pentest.
Assessments as part of ongoing security maintenance
Both vulnerability assessments and penetration tests are important tools for evaluating the security of a computer system. However, they are used for different purposes and provide distinct types of information. Vulnerability assessments are usually used as a first step in securing a system, to identify potential vulnerabilities that need to be addressed. While a penetration test is typically used as a last step. Used to confirm the identified vulnerabilities during the vulnerability assessment can be exploited and can represent an actual risk.
It is essential to note that vulnerability assessment and penetration testing are not one-time events and should be done regularly to ensure that the security of a system is up to date.
Invest in defensive AND offensive cybersecurity services
In addition to defensive measures, offensive cybersecurity services like vulnerability assessments and penetration testing can help you identify and address vulnerabilities in your systems. Don’t leave your organization vulnerable to cyber-attacks – contact us to schedule a cybersecurity assessment today.




