| Vendor |

|
| Product | Plugin Restaurant Solutions Checklist |
| Affected Version(s) | 1.0.0 and probably prior |
| Tested Version(s) | Wordpress 5.9.3 |
| Vendor Notification | 02 June 2022 |
| Advisory Publication | 02 June 2022 [without technical details] |
| Vendor Fix | N/A |
| Public Disclosure | 28 February 2024 |
| Latest Modification | 28 February 2024 |
| CVE Identifier | CVE-2024-1977 |
| Product Description | The Restaurant Solutions - Checklist allows create an interactive list for your managers to use that saves and stores a report the moment they click send. Then, you can consult any list from any day at any time. |
| Credits | José Adán Hernández F. Security Researcher & Penetration Tester @wizlynx group |
| Stored Cross-Site Scripting (XSS) Vulnerability in Restaurant Solutions – Checklist 1.0.0 | |||
| Severity: Medium | CVSS Score: 5.4 | CWE-ID: CWE-79 | Status: Open |
| Vulnerability Description | |||
| The Restaurant Solutions – Checklist plugin is affected by Stored Cross-Site Scripting (XSS) vulnerability affecting version 1.0.0. An attacker can use the vulnerability to inject malicious JavaScript code into the application, which will execute within the browser of any user who views the relevant application content. The attacker-supplied code can perform a wide variety of actions, such as stealing victims' session tokens or login credentials, performing arbitrary actions on their behalf, and logging their keystrokes. | |||
| CVSS Base Score | |||
| Attack Vector | Network | Scope | Changed |
| Attack Complexity | Low | Confidentiality Impact | Low |
| Privileges Required | Low | Integrity Impact | Low |
| User Interaction | Required | Availability Impact | None |
The Restaurant Solutions – Checklist plugin is affected by Stored Cross-Site Scripting (XSS) vulnerability affecting version 1.0.0. due to the lack of input validation and output encoding.
Using the "Add new checklist"
section it is possible to add a "checklist points", with the payload
"<img src=test><svG onload=alert(123)>".
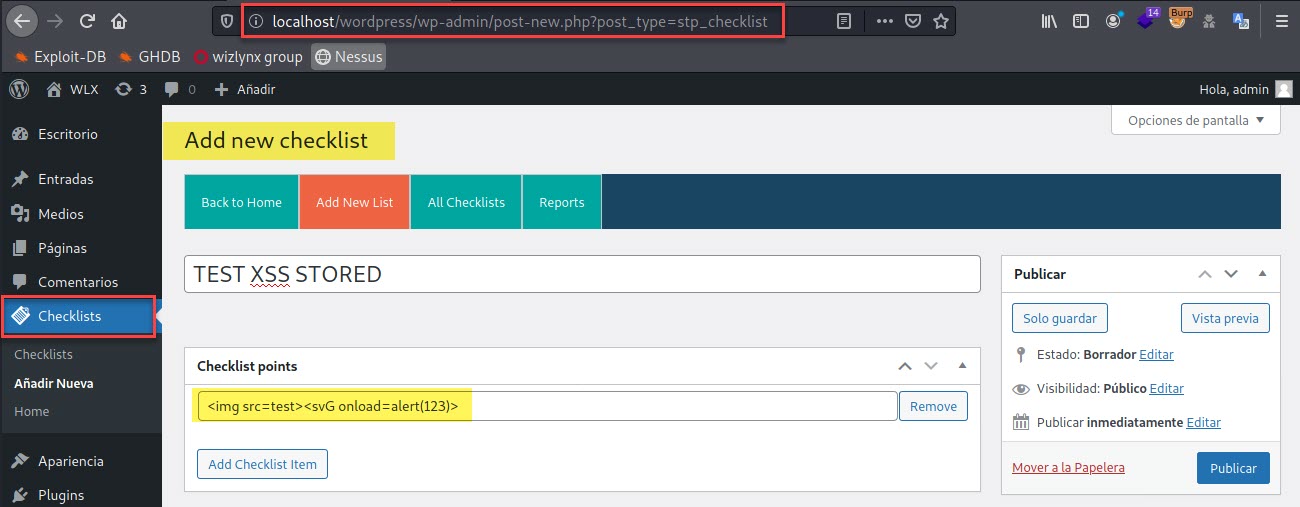
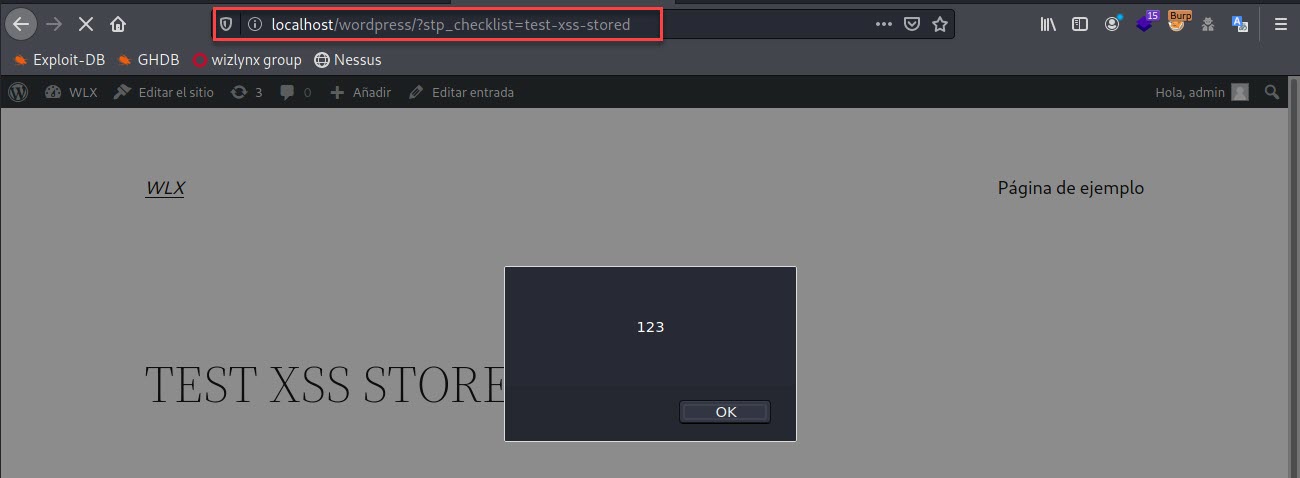
In the following image we can see that the injected payload has been saved correctly.
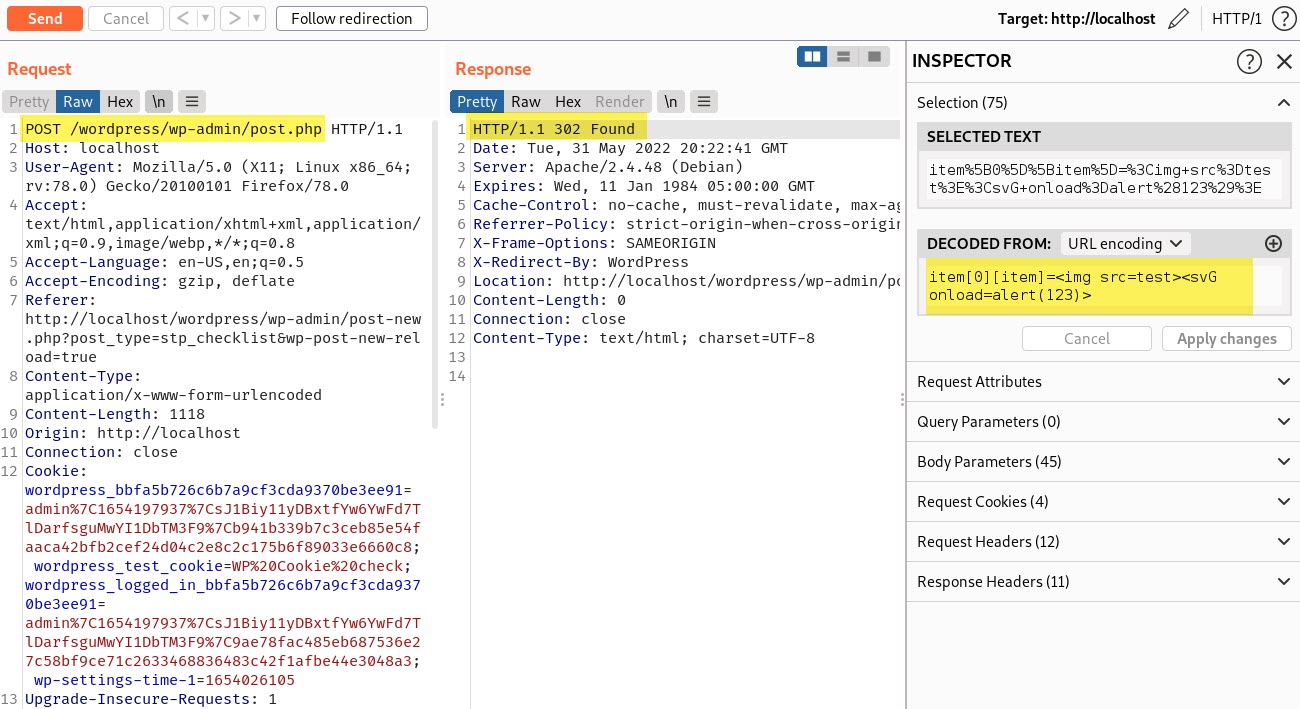
In the image below we can see that our checklist has been created, giving us a url to visit the registry.
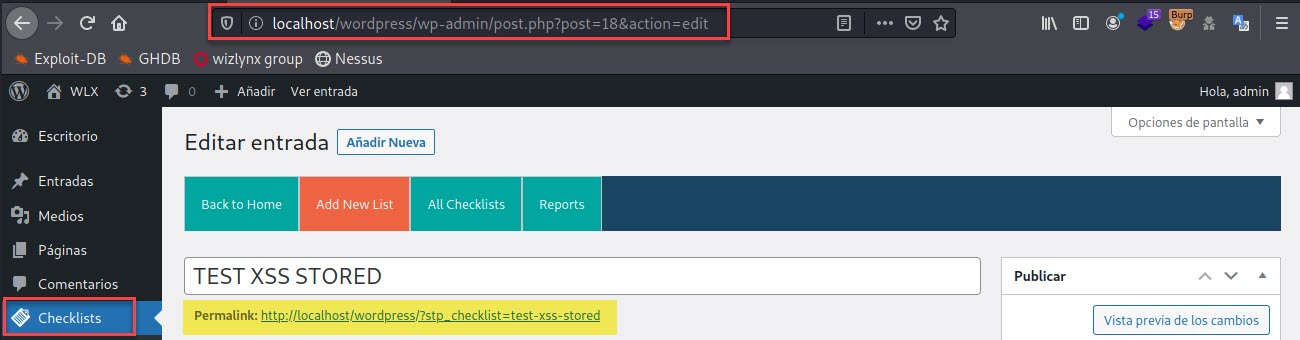
Finally, the following screenshot shows the successfully executed XSS payload.