IT Security
Because cyber threats keep evolving every day, an organization's information infrastructure and access controls must also evolve to avoid security breaches.
It is very difficult for companies to keep the pace and stay updated in terms of infrastructure and knowledge in order to effectively identify and eliminate new threats.
More times than not, the information security efforts emerge from different areas of IT, or even different departments within the organization. This causes efforts to be dispersed and work in silos, which ultimately leads to higher spending and impacts the effectiveness of the overall security strategy. We can help you integrate your actual security ecosystem, so it works as a single unit.
To help you stay safe, wizlynx expert consultants can:
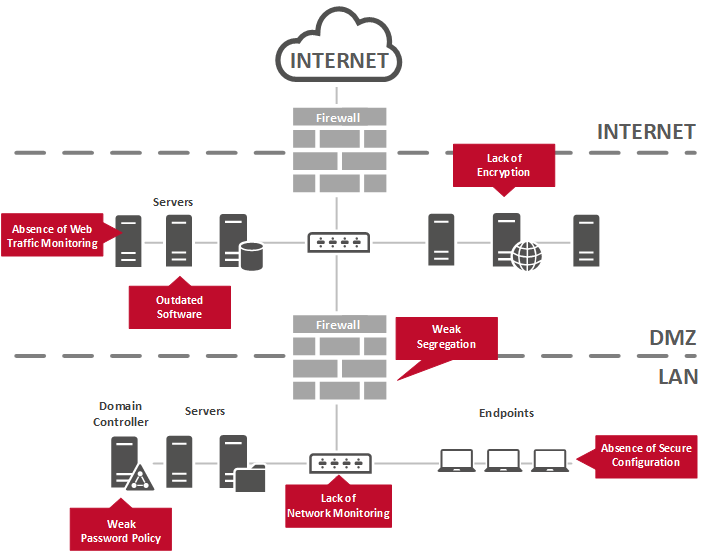
IT Security has become today’s biggest concern for every company, as IT Systems are becoming more diverse daily. In addition to in-house networks needing to be protected, remote workers, partners, suppliers and Cloud implementations run an increased risk of being attacked.
The demand for various Managed Services comes as a result of a broad range of needed Infrastructure, as well as emerging technologies. With our vast experience and high Swiss-quality service, wizlynx ensures compliancy with industry standards for Security (e.g. ISO27000) and IT Service Management (e.g. ITIL/ISO20000). Choose one or more of our Cyber Defense Managed Services, which can be operated independently of each other. Enjoy added values by outsourcing your complete Infrastructure/Security Management to the experienced and skilled engineers of wizlynx.
wizlynx group’s Managed Security Services provide an all-in-one package to ensure your employees and assets are safe and secure, allowing you to focus on your core business.
Our Managed Security Services rely on highly skilled security professionals with extensive experience in both defensive and offensive security, and holding the most recognized certifications in the industry.
Having protected "fortune 100" customers against all kind of cyber threats and having performed hundreds of security assessments and penetration tests, incident responses, and breach root cause analysis for companies in various sectors, wizlynx is the perfect partner to help you defend your network against evolving threats.
We offer management for a wide range of Security Devices such as:
Our provision of end-to-end Managed Security Services (MSS) for security devices includes the following activities:
Our Service Delivery Model ensures the choice of granular service items, even within each Managed Service. All managed security services are built on the ITIL v3 Standard to make sure the service will be delivered at the expected quality, as well as in accordance with an agreed-upon frame contract and SLAs.
Choose a fully outsourced Service including Monitoring, Global Service Desk and all instances of Service Delivery, or request only the parts which will ideally enhance your internal IT organization.
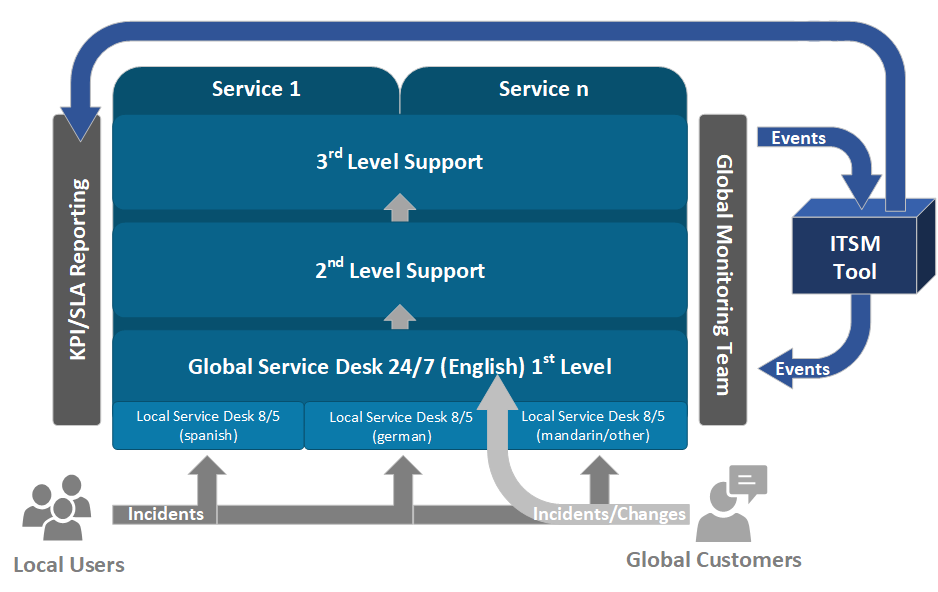
Our Service Delivery Model ensures the choice of granular service items, even within each Managed Service. All managed security services are built on the ITIL v3 Standard to make sure the service will be delivered at the expected quality, as well as in accordance with an agreed-upon frame contract and SLAs.
Choose a fully outsourced Service including Monitoring, Global Service Desk and all instances of Service Delivery, or request only the parts which will ideally enhance your internal IT organization.
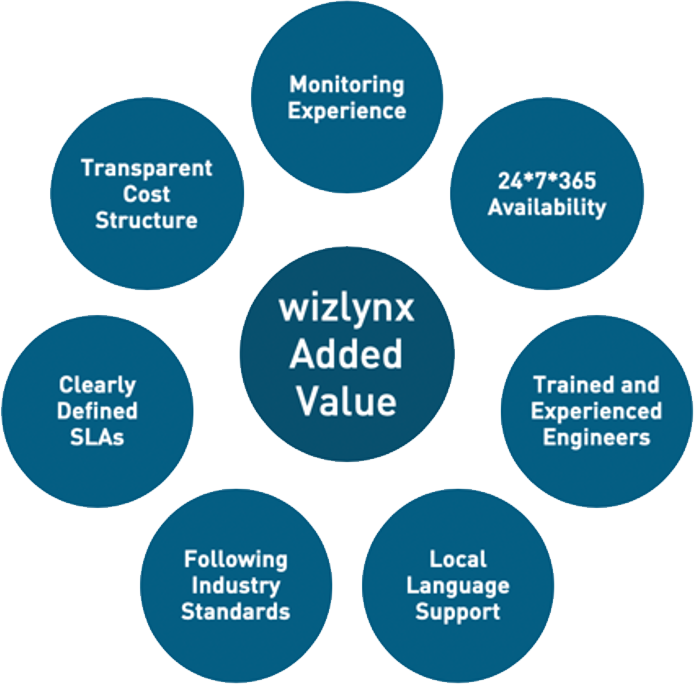
Our MSS team, which includes the management of all monitoring systems, is available 24/7 to ensure your infrastructure and data are protected, even when you are not working. wizlynx continuously improves the security implementations and provided Services, so you can always benefit from the highest quality and most secure services in the market.
Large enough to serve global enterprises, wizlynx remains flexible in handling all customizable service needs. Using efficiency and experience, we are able to implement new services/update current live services without disrupting your daily operations.