The internet has been invented for a while now. It connected people, images, recording, games, books, and commerce. By people, for people. With the Internet of Things (IoT) now, it is not anymore just about connecting people, but about connecting things.
There are already many fields of application within IoT: they range from house alarm systems monitoring and sending alarms to smartphones to bracelets collecting health records and submitting them to a physician. There are already cars constantly monitoring the environment and suggesting, or even acting, on behalf of the driver. Among other things, these cars can pre-calculate parts failure and scheduling the appointment for maintenance with the garage. On the home technology area, there are connected households calculating the optimal wake up time, starting to lift the room temperature, lighting up smoothly the room illumination and triggering the coffee machine to prepare the morning coffee. Refrigerators are reminding the owner to purchase items, or office equipment automatically re-ordering supplies when they run low. IoT is expected to offer advanced connectivity of devices, systems and services that goes beyond machine-to-machine communications (M2M), and clearing a variety of rules, domains, and applications. We will be surrounded with smart phones, smart cars, smart clothes, smart homes and offices, smart streets and cities. There are endless opportunities and interfaces with IoT we cannot even imagine.
What Exactly is IoT?
Gartner analyst described IoT “as the network of physical objects containing embedded technology to communicate and sense or interact with their internal states or the external environment”. Actually, IoT refers to the interconnection of embedded computing-like devices within the Internet. Most of these devices have embedded operating systems and are connecting to the Internet. All this introduces a huge range of opportunities for users and enterprises. Forecasts on the IoT device growth are drifting apart enormously. Gartner forecasts that in 2020, there will be over 26 billion IoT devices connected to the internet. Other sources, such as ABI Research, are saying that the number of device could reach 30 billion, and some sources even believe the devices will exceed 80 billion. However, all agree that we will experience an explosion of connected possibilities.
The IoT marketplace is still in its beginning, but there is a positive outlook of offering the user commodity and a more convenient life style. All this is about big data and big business. New markets will prevail.
IoT Security and Privacy – the Other Side of the Coin!
There is another side of the coin in relation to IoT. It is related to security and privacy. We learned already about ‘hijacked cars’, or about the risk of medical devices vulnerable to hacking. These, and hundreds of other disclosed episodes, are waking up the entire IoT industry. Vulnerabilities within IoT are opening up new possibilities to hackers. The number of IoT devices is exploding exponentially, which means the attack vector increases exponentially. In combination with billions of unprotected vulnerable devices, this state is alarming the security pros. The term “Cyber Thread” takes on a different dimension. Business continuity is jeopardized, and under certain circumstances, even life and health can be put at risk. Eugene Kaspersky, Chairman and CEO of Kaspersky Lab went so far and said that “… the IoT, which normally stands for the ‘Internet of Things’, should really be called the ‘Internet of Threats’ because IoT devices are going to vastly expand the ways in which hackers can get to you and your information”.
The IoT Industry has A lot of Work to Do
One can recognize that a joint effort of the IoT industry, the consumer and enterprise is necessary to look forward to a reasonably secure IoT future. However, I am afraid this will not be very easy and will take some time. Why am I saying this?
Of course, security companies and manufacturers are starting to cooperate to secure the IoT industry before it spins out of control. As example, digital security company Gemalto is planning to use its experience in mobile payments to help secure IoT devices. Microsoft is also committed to add BitLocker encryption and Secure Boot technology to the Windows 10 IoT.
However, it has to go further. Security and privacy has to become integral part of the development process of IoT concepts. Many of the IoT devices today have an embedded OS, which is not designed with security as a primary consideration. Numerous IoT devices are crowd-funded by people with little knowledge of security. The consequences are failure or bugs in the software or hardware. The devices have often no smart mechanism for automated software or security updates, if any, or no access control and permission mechanisms and no privacy policies. It is very much the Wild West. All this has to change.
And the Consumers?
In addition to the IoT industry, the consumers must take action, too. They must apply best practice security levels on the available resources. They must secure passwords on all devices, as well as regularly maintain and patch the devices. However, we know how difficult it is to raise the awareness about security and privacy on the end user side. Once again, the IoT device industry has quite a bit of work to do in this respect.
What Can We Do To Protect our Corporations?
We learned that the challenge and the homework needed to address these challenges are enormous. Because of the enormous potential of IoT for business efficiency and productivity, there is a big risk that business’s productivity rules out over Security. C-level managers may force adoption of IoT devices, regardless of the security risks. Also, there is a huge risk of IoT cross-contamination within the corporate network. Several IoT devices need to be plugged into computers via USB for charging, synchronization and update. Some are using ‘smart hubs’, which once compromised, can take over control of all connected devices.
Bruce Schneier, an internationally renowned security technologist wrote in his February 2016 “Security Blog”: “The Internet of Things will be the world’s biggest robot, and we don’t even realize it”. Placing an IoT device without additional consideration within the heart of our infrastructure is like letting in a Trojan horse in the internal, often very well protected, perimeter. Once compromised, IoT devices allow for criminals to perform reconnaissance in an enterprise network. At this point, the entire hackers tool box is at their disposal: scanning, exploitation, passive and active sniffing, session hijacking, password cracking, keeping access, propagating further Trojan backdoors, gaining remote control, internal DDoS attacks, denial of service.
So, what can we do? Define and apply the best IoT Security Practices. If you are considering to install IoT devices, craft an IoT security strategy first. To start, address all gaps, such as the patch gap or access- and permission control gap. Include a good identity and access management program with your IoT program for central user control. Search for standardization. This is only in its beginning stages now, but the market will soon define standards for the IoT, including security standards.
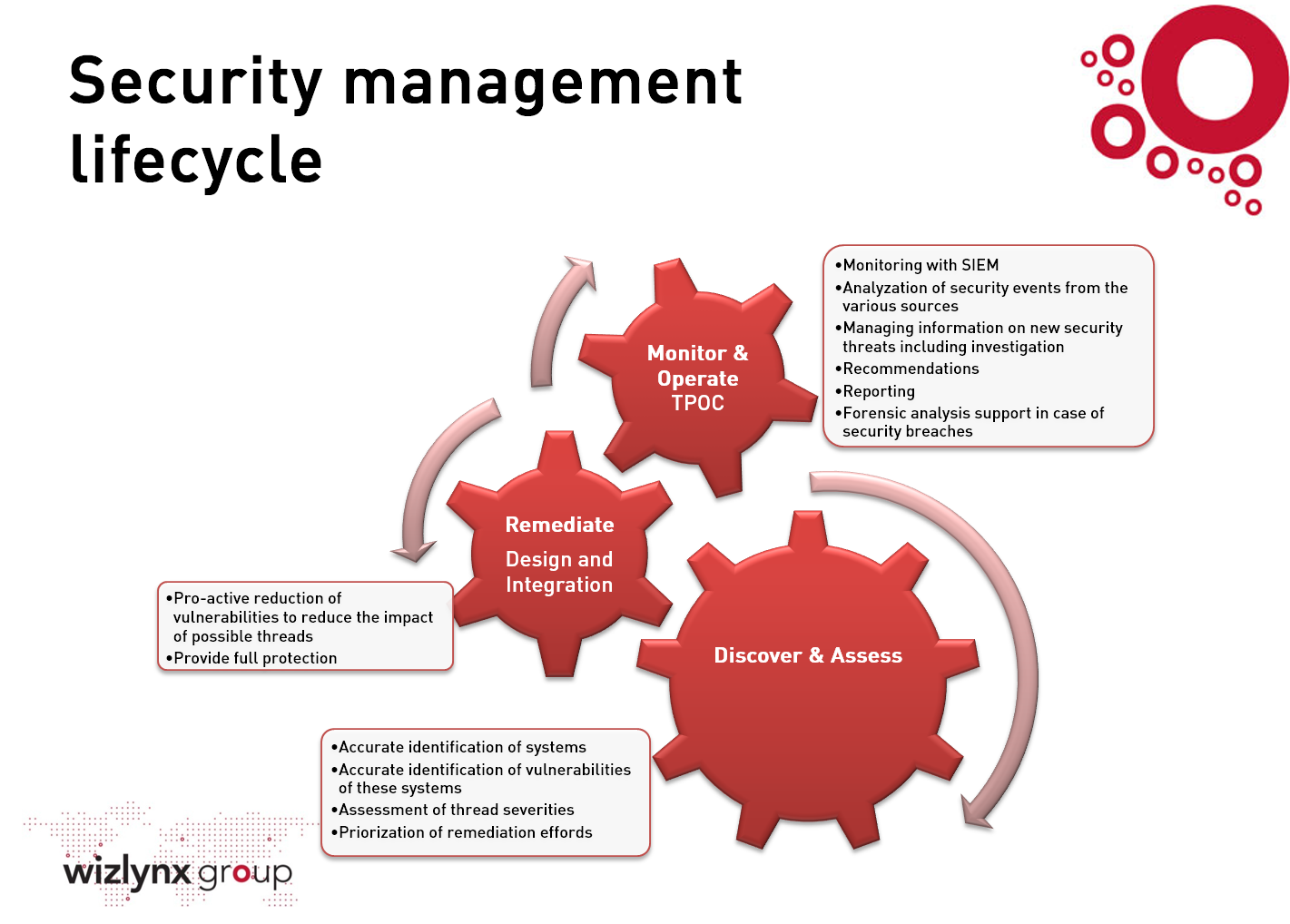
Last but not least: Think outside the firewall. Design a good perimeter protection with a firewall and an intrusion prevention system. Test the efficiency of your systems through periodical pen tests and security assessments. Consider and include everything in a security information and event management environment (SIEM). Implement an emergency response program. Actively practice the Security Management lifecycle: Discover & Assess, Remediate and Monitor & Operate.
So, can the Smart Refrigerator compromise the Security of our Corporation?
Eugene Kaspersky, said at the World Economic Forum 2016, which agenda was the rise of robots: “The landscape of cyber-threats is becoming increasingly complex, and we’re investing a lot of effort into staying a step ahead of advanced cybercriminals. A growing number of business transactions are carried out with mobile devices, and a huge amount of sensitive data is stored in them; all this makes them high-profile targets for criminals“. He then closed by saying, “A system is only secure if the potential expense of hackers is greater than the potential harm.”
The cavalry will not come to help us. We are the cavalry, but we can only do it with a common effort. We need strategies, awareness, manufacturers, resources, teammates, connections. While we share our concerns, we will equally share our outcomes to look forward to a secure IoT future.
By Andreas Crisante, Senior Cyber Threat Intelligence Advisor at wizlynx group