The Dark Web is a very mysterious place and very difficult to access…Nah – just kidding! Today’s media outlets are perhaps giving that impression, but accessing the Dark Web is truly at the reach of each and every one of us.
Before we give any details about the Dark Web, let’s start by explaining exactly what it is. As of today, the web as we know it is divided into three sections: the Surface Web, the Deep Web, and the Dark Web. The Surface Web and Deep Web are sections of the web we access on a daily basis. The Surface Web is accessible to anybody – news outlets, video streaming sites, social media sites, etc. The Deep Web is not as accessible as the Surface Web since we are referring to websites that limit access to their pages in a technical way (password-protected resources, etc.). Typically, accessing your private emails or the HR portal of your company would fall into the Deep Web.

The Dark Web is adding the concept of “anonymity” to both the client and service you are accessing. While we can simply use our browser to access the Surface and Deep Webs, the Dark Web can only be accessed via an anonymity service such as Tor, I2P, or the Freenet project. These anonymity services will hide both your IP address and service you are trying to reach. To strengthen the anonymity concept moreso, services and products on the Dark Web can primarily be purchased using bitcoins (a cryptocurrency and a payment system).
WHAT CAN YOU FIND ON THE DARK WEB?
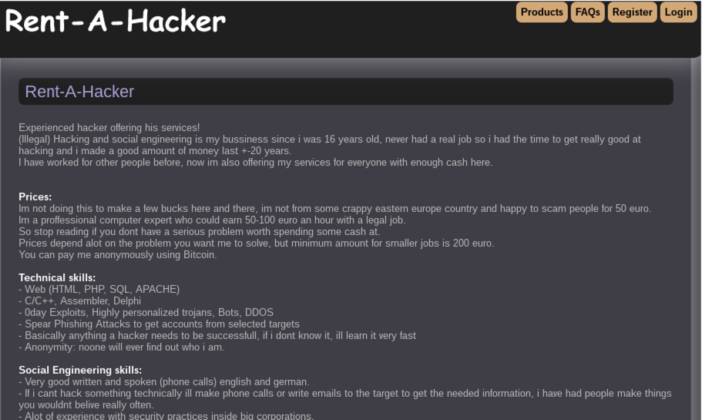
Now you will ask, what can you do on the Dark Web that requires full end-to-end anonymity? The answer is actually quite a few things. The Dark Web can be considered the “Alibaba cavern” where you can findanything illegal. One can surf on hacker forums, buy data dumps of successful hacks, hire hackers, hire hitmen (yes, hire hitmen!), buy weapons, drugs, and so much more!
For example, if your organization’s private information were to become compromised, and sensitive documents were leaked, or your employees’ accounts werestolen, these types of data would most likely end up for sale on the Dark Web.
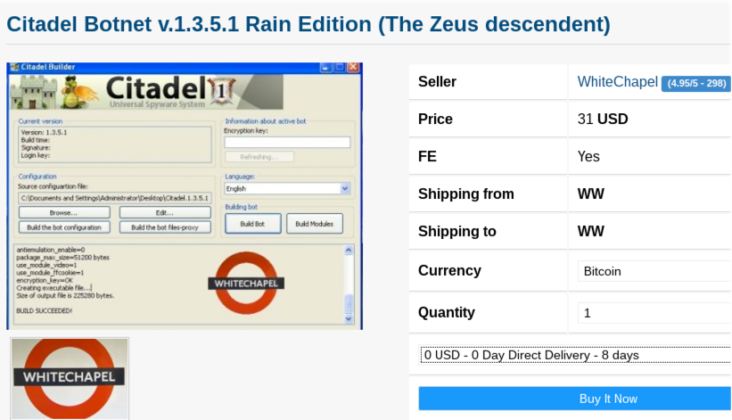
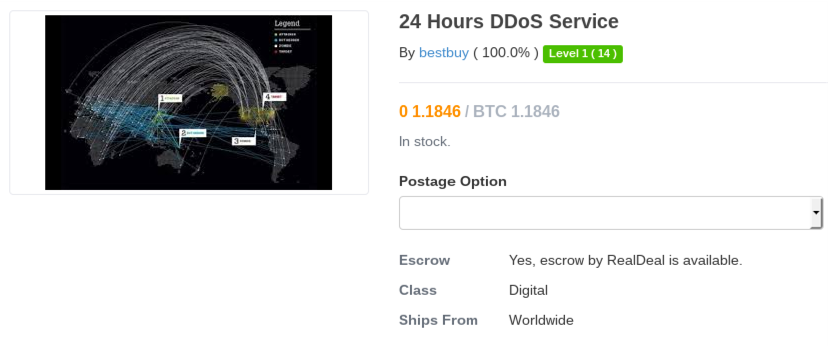
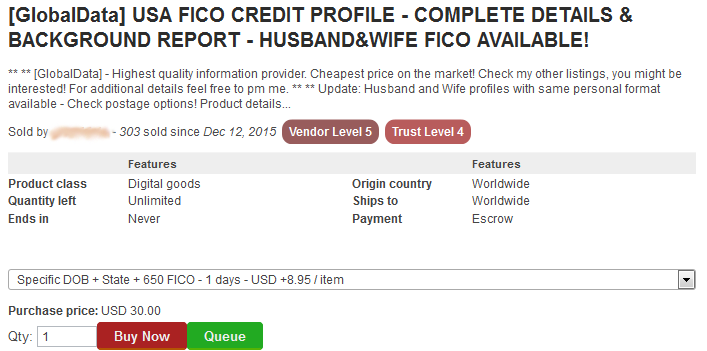
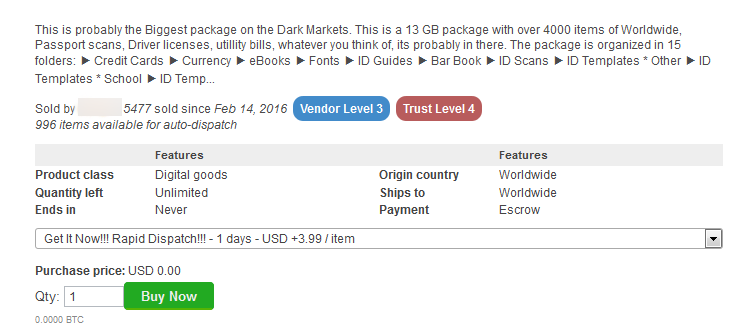
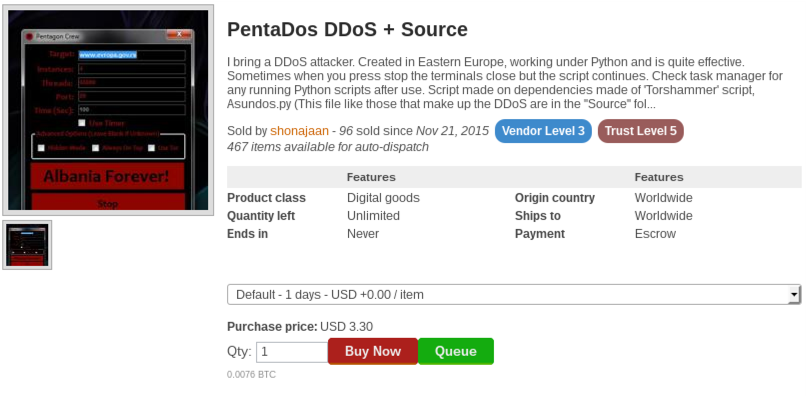
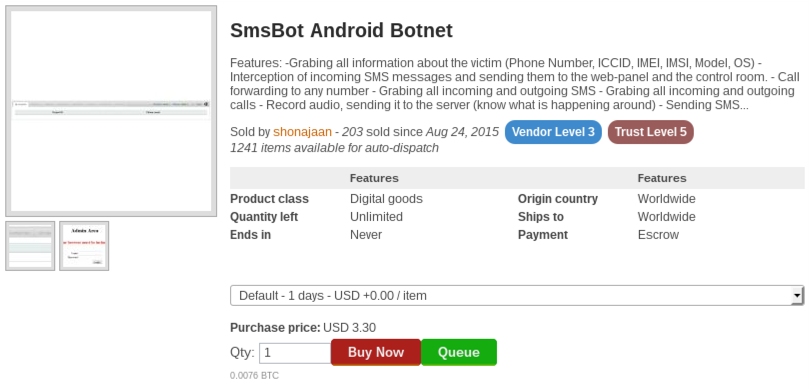
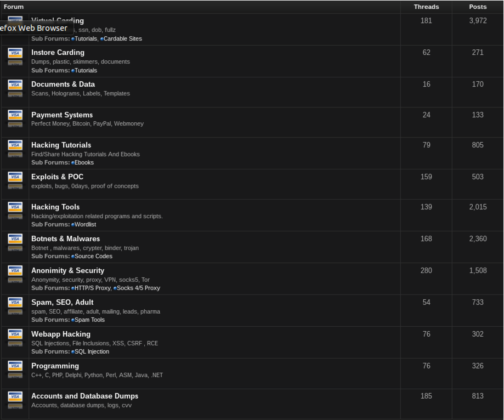
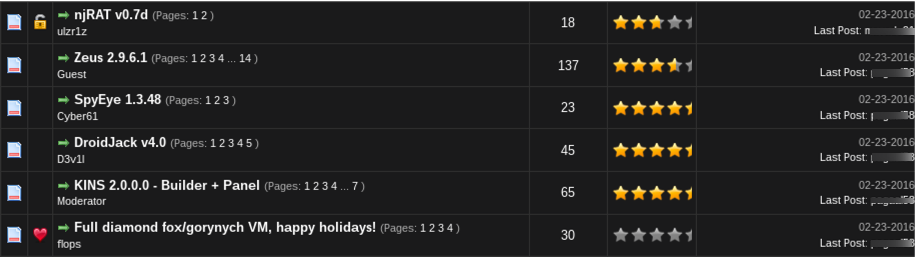
Below are more examples of other items and services you can buy on the Dark Web:

For further entertainment, please find an image gallery below of screenshots taken from various places on the Dark Web:
HOW CAN YOU LEVERAGE THE DARK WEB’S INTEL?
Imagine if you could keep an eye on the cybercriminal and see what they are planning! You could:
- Get latest cybercrime trends by watching what is being sold on marketplaces
- Gain even more visibility into the latest malwares, exploits and threat vectors
- Identify your organization’s confidential documents; employees’ account on the Dark Web can be used as an Indicator of Compromise (IOC)
wizlynx has released a new service that removes the complexity and automates the collection of information on the Web, Deep Web, and Dark Web.
Our Targeted Cyber-Threat Intelligence (CTI) solution is collecting information on a continuous basis on closed/proprietary sources within the Dark Web. Examples of sources include closed forums and marketplaces, criminal infrastructure hosting malicious attacks, and hacking & underground forums including zero-day exploit forums.
The following are some of the use cases of our CTI Services:
- Identify compromised accounts and computers by recovering credentials from a diverse range of sources, protecting your organization from potential damage, such as becoming part of a botnet network, data theft, or other cyber threats
- Detect stolen credit card information when published and sold on black markets to protect your customers or employees from becoming victims of fraud
- Limit damages of a successful hack by discovering whether your organization’s confidential information or even trade secrets have become publicly available on the Internet, peer-to peer networks and the Dark Web
For more information about wizlynx Targeted Cyber Threat Intelligence Solution go to wizlynx CTI Services