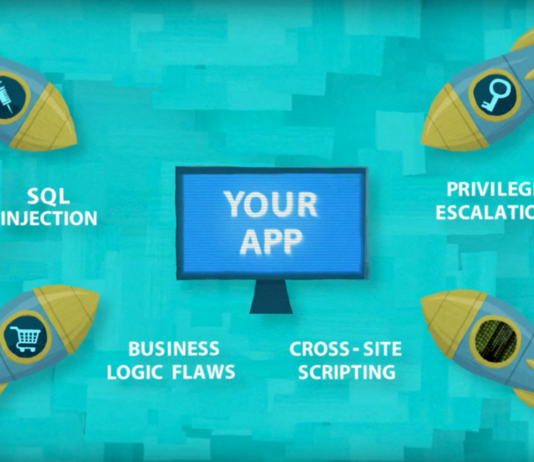
Effectively Securing Your Corporate Web Applications in 5 Steps
According to the latest Verizon Data Breach Investigations Report, cyber-attacks are on the rise. The cat-and-mouse game between hackers and defenders of corporate web...
PwnTillDawn Mexico 2019
On the 6th of April 2019, wizlynx group hosted its first computer hacking competition, PwnTillDawn in Mexico City. Part capture the flag...
Social Engineering & Email Phishing – The 21st Century’s #1 Attack?
Together with your
internet-facing web apps, you are undeniably the #1 target of a cyber attacker
to either break...
WLX is now CREST accredited Penetration Testing Provider GLOBALLY!
Based on the great success of wizlynx group in the Asia Pacific region providing CREST accredited penetration testing services, we decided to extend our...
Digital Transformation
The example of digital transformation studied by Digitalya, and available on their blog (see link below) is...
PwnTillDawn Online Battlefield – New Features and Improvements
Our CTF style Penetration Testing lab, PwnTillDawn Online Battlefield just got some awesome new features and improvements we are sure you will...
The Rise of Artificial Intelligence in Cyber Security
Currently, the new trends in cyber security are the use of artificial intelligence (AI) and machine-learning to predict threats before they are even conceived....
Cyber-Threat: Just a buzz word or a real risk for your...
A sober reflection on the facts delivered by Verizon with their annual “2016 Data Breach Investigations Report (DBIR)”
For the last few years, we read...
Banking Trojans – An Immortal Enemy
A few years ago, the best way for a criminal to prepare for retirement was to rob a bank by physically breaking in or...
Turning Point – Is Your Company Safe?
In today’s world, more and more companies are relying on cheap security services, lured by the low prices offered to them. In parallel with...